XML-RPC (XML Remote Procedure Call) is a feature which allows your website to communicate with other websites or apps, very similar to the modern REST API.
For WordPress Sites, XML-RPC enables external applications, such as the WordPress Mobile App and other functionality like receiving pingbacks when another blog or site has linked to you. Since 2015, WordPress has switched to the more modern ‘REST API’ which has effectively replaced and super-seeded XML-RPC making it no longer required for the vast majority of sites.
Reasons For Disabling XML-RPC on WordPress
Common reasons for wanting to disable XML-RPC are:
- Help prevent Brute Force Attacks: With XML-RPC enabled, an attacker can try to login to your site far quicker than through the web interface
- Help Prevent DoS (Denial Of Service Attacks): Abusing XML-RPC is a frequent method employed by attackers to take down your site or use your site as part of a large-scale Distributed Denial of Service Attacks against other sites
- Eliminate A potential Security Vulnerability: The fewer services you have enabled, the smaller the less opportunity you are giving an attacker to exploit a previously unknown vulnerability
Is It Safe To Block XML-RPC?
It is generally safe to block XML-RPC, however it should be done with some caution as it may impact the functionality of certain plugins, themes, or external applications.
The major plugin and reason you should not switch off XML-RPC is if you use JetPack, or the WordPress mobile app, however these can be whitelisted.
After blocking XML-RPC, it is strongly recommended you thoroughly test the site afterwards and ensure all plugins are working correctly. For more complex sites with integrations with other software packages it might be worth contacting the developer who build the site.
Alternatively you can review the traffic logs to look for calls to /xmlrpc.php and see if any of the requests are legitimate or from an IP address you are familiar with. In this case the traffic was from an unknown IP address and the site never even used xmlrpc to begin with!

Should you experience any issues, fixing the issue simply removing the block!
How to Block XML-RPC
The most efficient and secure way to block XML-RPC is by restricting the webserver letting traffic access it.
This can done by adding the following codeblock to the top of your .htaccess file located in the file directory of your WordPress site.
If you wish to allow certain IP addresses to continue to use XML-RPC, you can add these in manually such adding JetPack’s IP Address Range.
You can remove the 123.123.123.123 line in the provided codeblock if you do not want to whitelist any IP’s.
# Block WordPress xmlrpc.php requests
<Files xmlrpc.php>
order deny,allow
deny from all
allow from 123.123.123.123
</Files>Alternatively if you wish to use a plugin, options exist such as Disable-XML-RPC-API however additional plugins can slow down your site and create other issues.
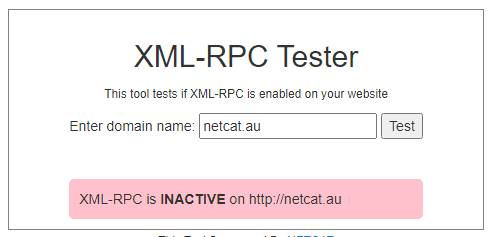
Verifying XML-RPC is Disabled
You can use our XML-RPC Testing Tool to verify if XML-RPC is disabled on your WordPress site.
If you have any questions with this, please feel welcome to let us know in the comments below.